
Map your external attack surface with additional intelligence on where your organization’s infrastructure is exposed on the dark web. Continuously monitor for compromised assets, vulnerabilities, and misconfigurations.
Outpace attackers: Real-time attack surface visibility, enriched with cyber threat intelligence – without the noise and complexity.

Secure your entire attack surface with Searchlight’s unified platform. Gain the ability to identify, manage, and mitigate external risks – from third-party vulnerabilities to bad actors on the dark web – all from a single pane of glass.
Spot Threats Earlier“We got more done for our security in three days using Assetnote than we have in the last four years using [competing platform].”
Law enforcement at all levels – from local and state police, to special units, to federal and international agencies – use our dark web investigation tools to uncover dark web criminality, collect evidence, and ultimately bring criminals to justice.
Bring Criminals to Justice“It gives investigators a statistical overview of marketplaces in a blink of an eye.”
Join the MSSPs enhancing their services and unlocking new revenue streams with dark web intelligence. Our partner program and product suite are built to match MSSPs’ business models and technology requirements.
Unlock Revenue Opportunities“Preventive cybersecurity will become increasingly important for businesses in the coming years and the addition of the pre-attack intelligence provided by Searchlight Cyber complements the growth of the more conventional protection market, such as SOC and EDR.”
We help government agencies to gather intelligence and intercept communications, giving them an operational advantage over human traffickers, drug cartels, and terrorist groups operating on the dark web.
Gain the Tactical Advantage“We were blown away by the robustness of the platform and its features, and could immediately see the value that dark web intelligence would add to our cybersecurity toolset.”

Assetnote is the only ASM solution that scans your entire attack surface every hour, combining cutting-edge discovery, enrichment, and vulnerability research into a single. easy-to-use tool. This unique approach ensures you uncover hidden assets and subdomains and are alerted to risks before attackers can exploit them.
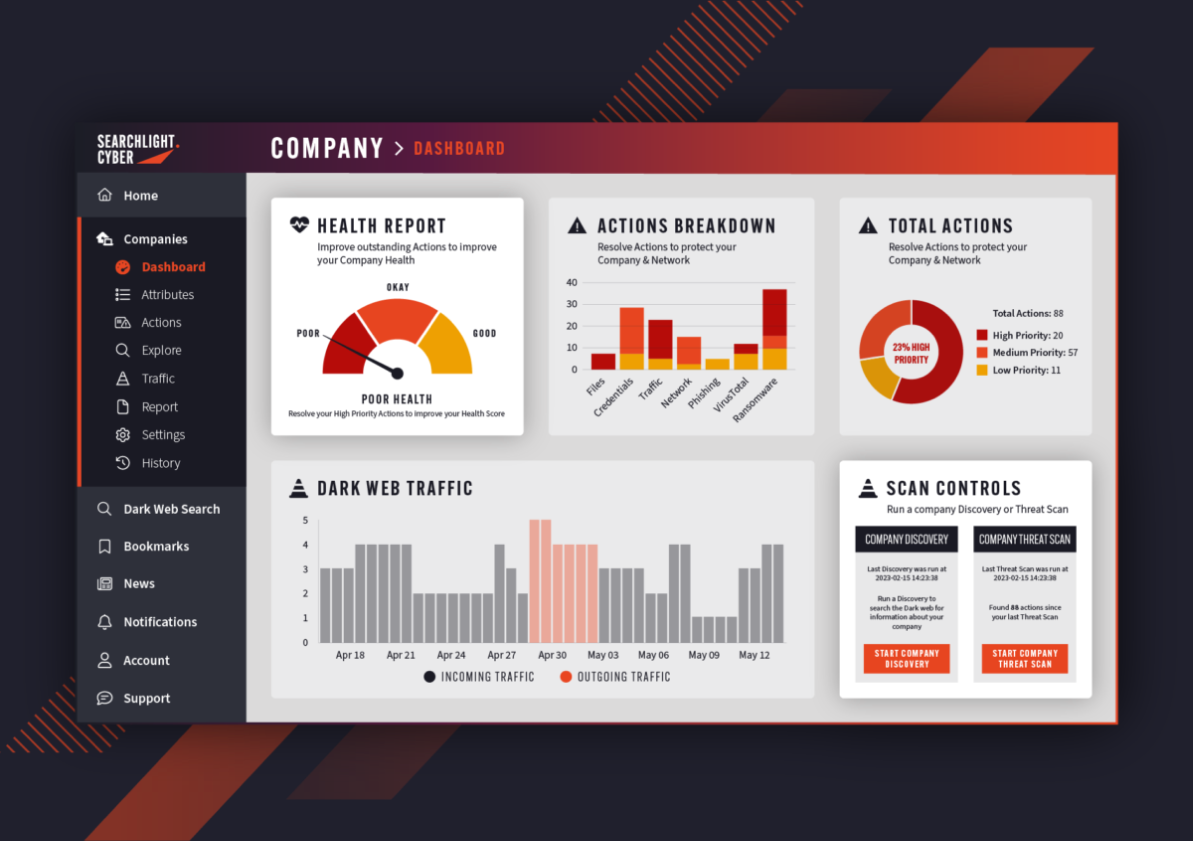
DarkIQ continuously monitors the dark web for threats related to your organization. It automatically cross-references your external attack surface against over 475 billion deep and dark web records, alerting your security team to threats such as leaked credentials, phishing sites, and dark web chatter in hacking forums, marketplaces, encrypted chats, and more.
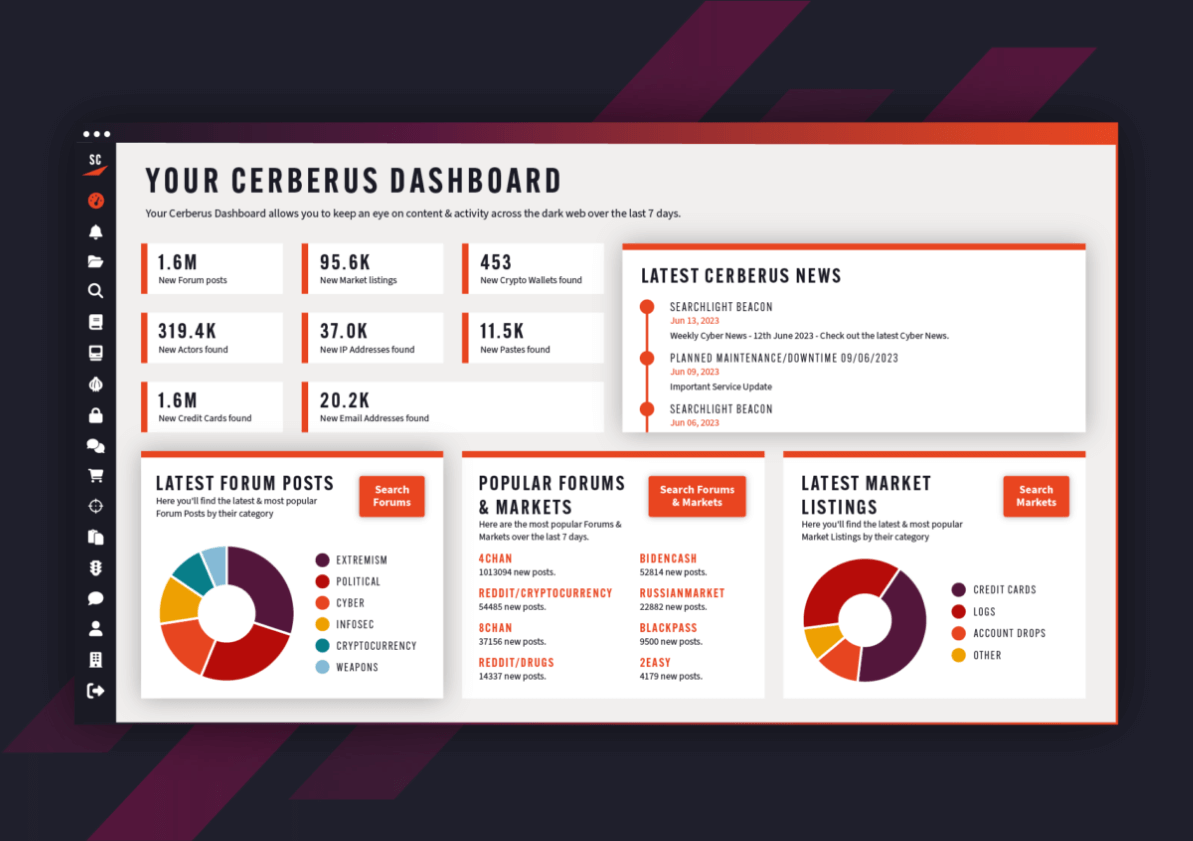
Built in collaboration with law enforcement and government agencies, Cerberus gives investigators and cybersecurity professionals access to more than 15 years of intelligence gathered from dark web marketplaces, forums, and leak sites. This data is updated in real-time and continuously archived, providing the most comprehensive platform on the market for investigating dark web criminality.
At Searchlight Cyber, our mission is simple – we build high signal and low noise tools to help defenders stay ahead of external threats. Our customers have access to best-in-class ASM, DRP, and dark web investigation capabilities, which allow them to regain the advantage over threat actors.
Why Defenders Choose Searchlight Cyber
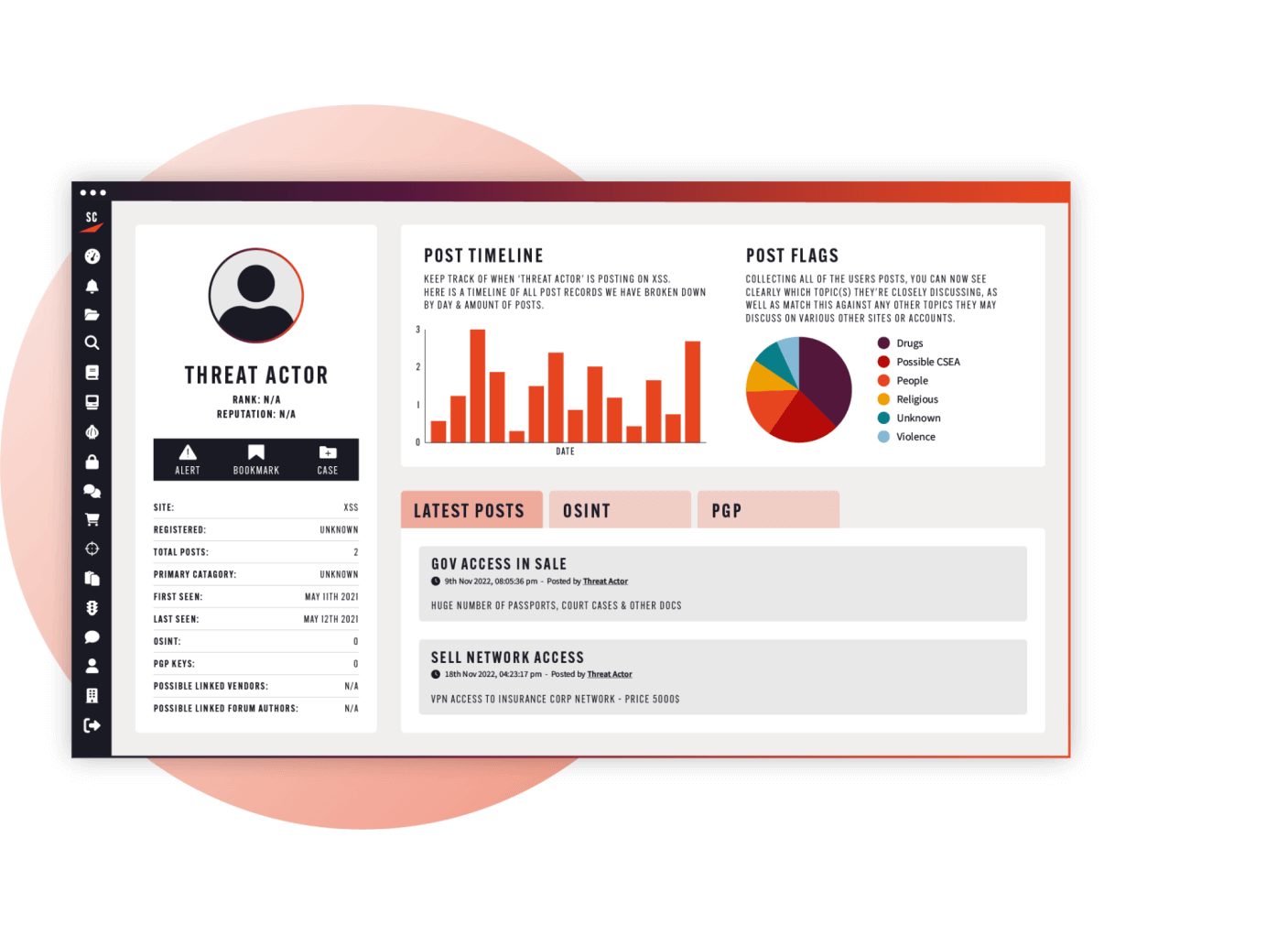
Searchlight Cyber’s external cyber risk management tools provide a holistic view of your attack surface, with critical dark web insights, alongside cloud assets and third-party risks, so you can stay ahead of external threats.
Our agentless tools help security teams focus on the threats that truly matter.
Our hourly attack surface scanning, combined with near-real-time monitoring for phishing sites, breached credentials, and dark web activity, ensures you detect and remediate exposures before they’re exploited.
Wasting time on false alarms slows teams down. Searchlight automatically detects and prioritizes version-specific exploitable exposures, so you can focus on real threats – cutting noise and improving response time.
Our dataset is automatically updated and archived, meaning data remains within our platform even if it has been deleted from the source. Access years of historic data for trends and intelligence.
Our team of security researchers and threat analysts constantly identify new vulnerabilities and gather threat intelligence, giving you early warnings on threats before they become active risks.
Unlock capabilities such as our Indicators of Compromise module, Dark Web Traffic Monitoring, Stealth Browser, and AI-Powered Translation to access pre-attack insights no other cybersecurity vendors provide.
Searchlight’s team works tirelessly to maintain access to closed sources including forums, paste bins, and encrypted communication apps such as Telegram, so you don’t have to.

Use the same products and dataset trusted by government and law enforcement organizations around the world to investigate criminality taking place on the dark web.
Arm your organization with access to +475 billion recaptured data points from the clear, deep, and dark web – data that was once difficult to track is now searchable at the click of a button. This enables you to capture evidence and identify threats earlier.
See What Threats You Can Uncover
850k+
Dark web sites

110+
Dark web marketplaces
210+
Dark web forums
Map your external attack surface with additional intelligence on where your organization’s infrastructure is exposed on the dark web. Continuously monitor for compromised assets, vulnerabilities, and misconfigurations.
Gather intelligence on criminals on the dark web. Identify illegal activity taking place within your jurisdiction, gather evidence on the individuals within the criminal organization, and bring them to justice.
Gather threat intelligence directly from the source: cybercriminals operating on the dark web. Inform your defenses in real time with first-party collection on your adversaries, their tactics, and their capabilities.
Determine the risk of a cyberattack based on your level of dark web exposure. Use Searchlight Cyber to identify where your organization is listed on the dark web, take steps to mitigate vulnerabilities, and reduce your cybersecurity risk.
Inform incident response planning with dark web intelligence. Mitigate cyberattacks faster with the ability to trace back cybercriminal actions from the dark web, through features such as Dark Web Traffic Monitoring.
Enhance your protection against ransomware with continuously updated intelligence gathered from ransomware groups’ dark web leak sites on their victimology and known associates operating on dark web forums.
Automated, continuous monitoring of the dark web can enhance your security operations by providing early warning of threats emanating from the dark web. Improve alert prioritization with dark web enrichment.
Monitor the dark web for any indicator that key partners and suppliers are being targeted by cybercriminals. Identify data leaks, supply chain vulnerabilities, or dark web chatter aimed at suppliers and take action.
Searchlight Cyber is used by security professionals and leading investigators to surface criminal activity and protect businesses. Book your demo to find out how Searchlight can:
Automatically discover and prioritize blindspots in your attack surface with ASM hourly scanning.
Enhance your external security with advanced automated DRP, ASM, and investigation tools in a single platform.
Prevent costly cyber incidents and meet cybersecurity compliance requirements and regulations.